The truth is that attacks will happen because the bad actors will always find a way in. It’s all about slowing cyber-attacks down enough to have them tire out and move on, anyone who tells you different isn’t being honest.
Phishing is a hazardous phenomenon for inexperienced internet users. In this case, the fraudsters pretend to be a trustworthy person in order to obtain confidential data. Nowadays, it should be noted that cybersecurity is not only the responsibility of the IT team - it is also a responsibility of employees.
One thing is important to note:
A quick response will allow you to stop the attack before it spreads throughout the network and cause severe damage.
Some essential tips to ensure safety:
- Do not open emails from senders that you do not know. If you decide to read it, be careful not to click on links or download any files.
- Never click links in emails unless you know exactly where they lead to.
- Find the website’s digital certificate.
- Don’t use anonymous public Wi-Fi networks.
- Do not leave confidential data on sites that do not provide a secure connection.
- Be careful with the attachments you receive. If you are unsure – better not open it.
- Check that the sent message does not contain language errors. Attackers do not prioritize quality of spelling and grammar.
Look for the “S” on websites you visit ( HTTPS://). When someone asks you to provide confidential information, make sure it has HTTPS in the URL/Web page. - If you suspect the email, copy the sender address or text from the message and check your browser search engine for known phishing attacks using the same info.
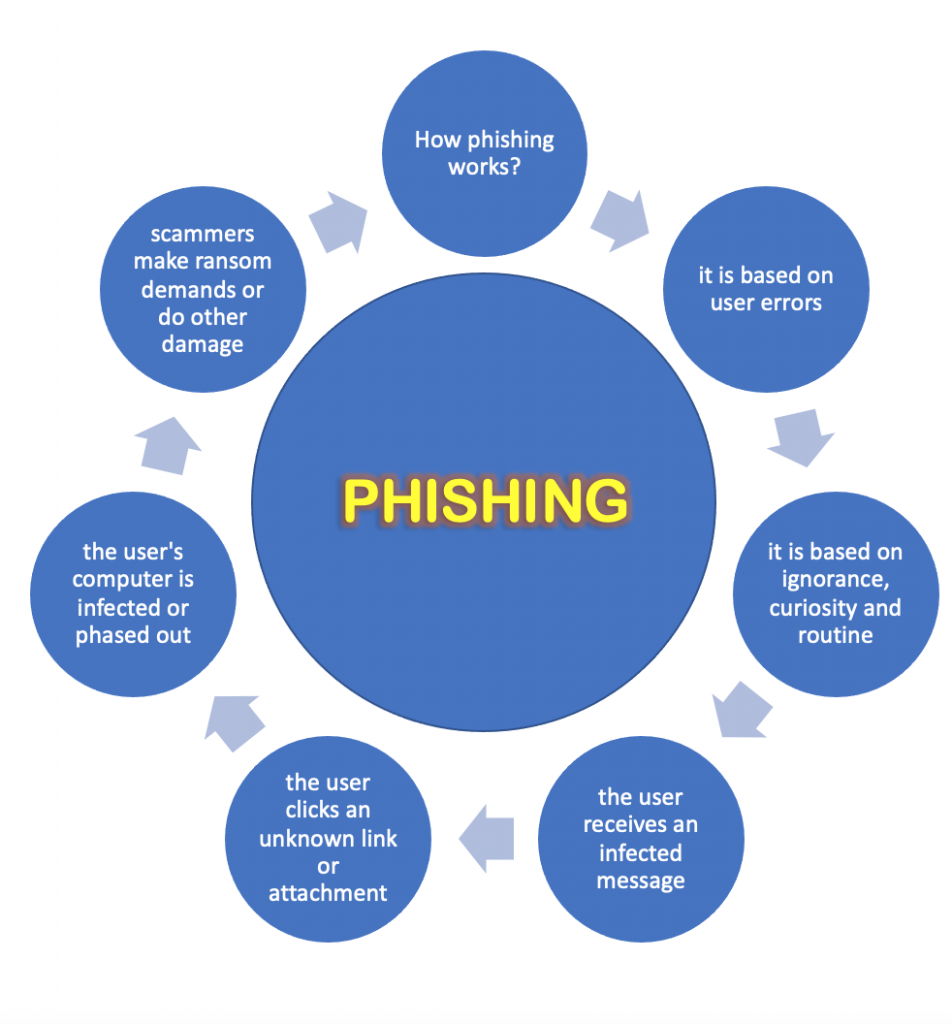
Anyone can become a victim of phishing. Criminals keep introducing new ideas to lower your guard. More and more organizations have to face this problem, and the best way to minimize the risk is to educate employees so that they do not fall for criminal fraud. The company should train employees and managers to recognize cyber threats and report them to the IT department as soon as possible as part of risk reduction. It is currently the best protection method against phishing.
Employees do not expose companies to attacks on purpose; they do it unknowingly or in a rush because of a lack of training and ignorance of what could be wrong - especially when they use a private online account for business purposes. Unassuming employees can connect scammers with a wrong click or even a reply to malicious messages, sending over confidential company data. Conclusion: All employees should know how to handle data, recognize techniques used by criminals, and report them to the IT department in time. Unfortunately, software alone is not enough to protect against cyberattacks because reliance on software without additional thinking and knowledge can be an enormous risk. The most common attacks are phishing because it is the easiest and most effective way to access sensitive company data. Just take a little more time to prepare your staff for recognizing scam and alerting your IT department so they can act as soon as they are informed. Cooperation with trained personnel and a thriving IT department will protect the company against unnecessary and costly consequences.
What important information about cyber threats should an employee know?
1. Using secure internet access points
Using Wi-Fi networks in inappropriate places is risky because cybercriminals can track users' activity online and take over data and passwords, e.g., banking. It is essential to have antivirus software, and it is worth having it on all devices connected to the network.
2. Separate work network
An excellent idea for working from home is to have a separate password-protected network. An independent system will allow confidential company matters to be separated from personal matters. This way it will be much more difficult for a hacker to use private applications and devices to enter the network of company system.
3. Regular updates
A busy lifestyle often causes one to ignore update notifications and postpone them, thus making it easier for hackers to do their job.
4. Strong passwords
Always use a strong, complex password containing numbers and special characters. It is essential not to use the same passwords on all devices and accounts. While the cybercriminal uncovers one of the passwords, he will not be able to target the others. To help you remember passwords, you can use special programs to manage them. New technologies also enable biometric authentication using fingerprint scanning or facial recognition.
5. Multifactor Authentication should be a standard layer of protection.
Unfortunately in today’s world, the password is usually not enough. Companies need to push for multi-factor authentication (MFA), which helps protect data by adding a layer of security. This makes it difficult for hackers to succeed without access to your mobile device.
6. Note on email
Electronic mail is one of the most popular tools used by cybercriminals and it is a simple way to spread malware through links or attachments. The rules of limited trust should always be kept in mind to be absolutely sure before clicking on any link or attachments. Also, pay attention to the name of the recipient and website. Very often there are spelling/grammar errors, so you should read carefully. Messages that you did not accept should be treated with extreme caution.
An essential element is a quick response to incidents and repairing the threat caused by an attack. The employee should know who to contact in the event of a security breach.
Run scheduled phishing campaigns and emergency training for employees regularly.
Our interactive phishing awareness campaign training can help you combat phishing threats.
We repel attacks in many ways:
- Business-class antivirus/malware
- Business-class firewalls
- Business-class security bundles that include:
a) Packet scanning
b) Sandbox filtering
c) Geo-clocking
- Alerts that tell us when someone is trying to get into your network
- Network scanning for new devices being added to your network
- Training
- Send out a phishing test to see who will fail to act accordingly
- Installing software that can lock unwanted and unneeded software from starting
- Monitoring your environment 24/7
Cybercrime is not a minor threat; it can have a devastating reputational and financial impact on your organization. Our holistic approach to cybersecurity allows us to assess all potential cyber threats from affecting your staff, your capital, and your technology. We will ensure that you are aware of the potential risks and take all necessary steps to mitigate them.
Call us today to learn how we can protect you against cyber-attacks.



