Password protection is a very simple element to help keep your business secure. A continuous and recurring problem is that people frequently use the same passwords, which can be easily guessed by malicious cybercriminals. Using simple passwords makes it easier for cybercriminals to access a wide range of accounts and information. Stolen information is most often made public and sold at a profit on the deep web. Therefore, implementing randomized passwords can make it much more difficult for criminals to break into your accounts.
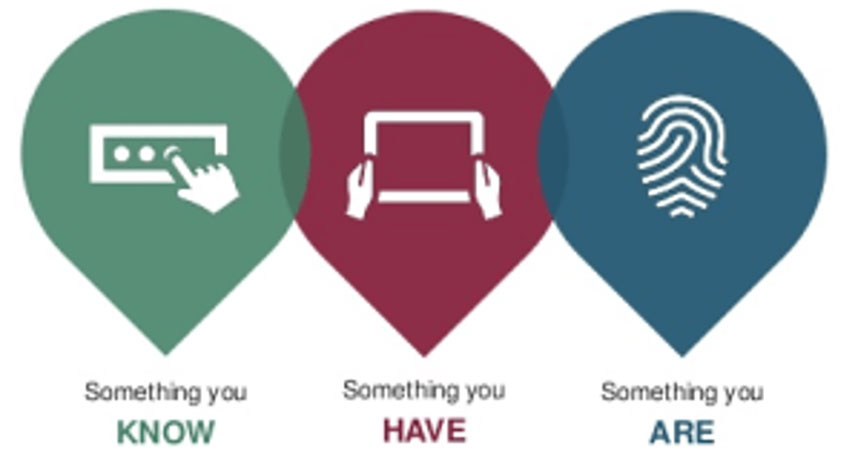
There are many authentication technologies (passwords, fingerprints, etc.) to verify a user's identity before allowing access. The key is to add extra layers of protection to prevent security holes such as data breaches. A combination of different types of authentication provides sufficient fortification of the system against possible threats.
 What are the types of authentication?
What are the types of authentication?
Authentication prevents invalid users from accessing databases, networks, and other data. These types of authentication use authentication factors, which are a category of credentials for confirming a user's identity.
Single-Factor/Primary Authentication
The most common form of authentication, Single-Factor Authentication, is unfortunately the least secure as it only requires one factor to fully access the system. It can be a username/password, a PIN number, or some other simple code. Although user-friendly, single-factor authentication systems are easy to infiltrate through phishing, key logging, or mere guesswork. Since there is only one authentication gateway to go through, this approach is very vulnerable to attacks.
Two-Factor Authentication (2FA)
By adding a second factor to your verification, two-factor authentication strengthens your security. This is an extra layer that basically double-checks that the user is in fact the real user trying to log in to, making it much harder to break into. With this method, users enter their basic credentials (username/password) and then have to enter additional identifying information.
The second factor is more difficult because it requires something unrelated to the system that the user can access. Possible secondary factors are a one-time password from an authenticator app, a phone number or device that can receive push notifications, an SMS code, or biometrics such as a fingerprint (Touch ID), face (Face ID), or voice recognition.
2FA greatly minimizes the risk of a system or resource being compromised as the invalid user is unlikely to know or have access to both authentication factors. While two-factor authentication is now more widely used for this reason, it does cause some inconvenience to the user, which still needs to be considered when implementing it.
Single sign-on (SSO)
With SSO, users only need to log into one application to access many other applications. This method is much more convenient for users as it reduces the need to store multiple sets of credentials and ensures smooth operation during sessions. This process enables domain-monitored user authentication - by signing out once, it can ensure that legitimate users are successfully logged out of all connected resources and applications at the end of the session.
Multi-Factor Authentication (MFA)
Multi-factor authentication is a method that offers a high degree of certainty as it uses more non-system-relevant factors to verify users. Like 2FA, MFA uses biometrics, device-based confirmation, additional passwords, and even location or behavior-based information (keystroke pattern or typing speed) to confirm a user's identity. The difference is that while 2FA only ever uses two factors, MFA can use two or three with the ability to differentiate between sessions. This adds additional barriers to entry for invalid users.